[This post was originally submitted by Nader Helmy to DIF's medium.com]
Technology
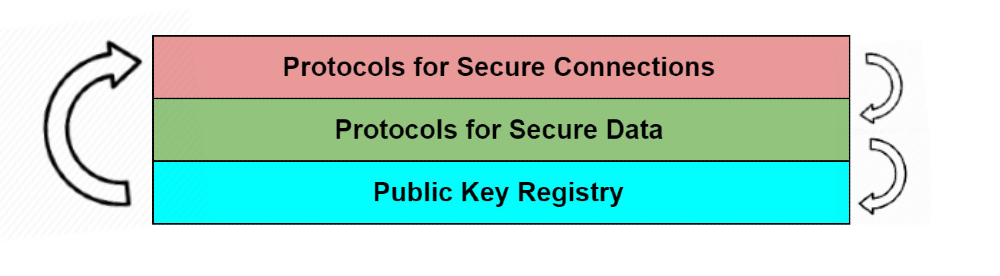
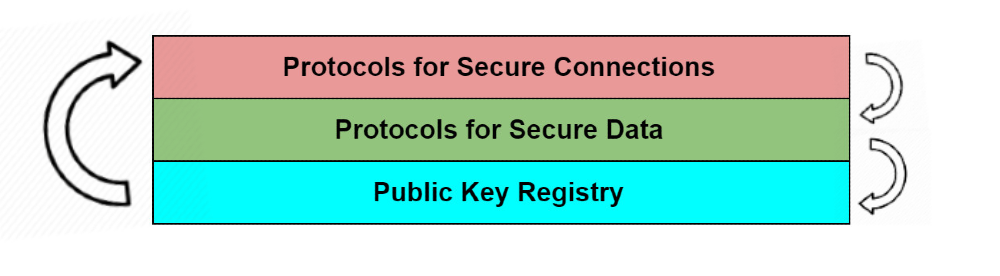
- A standard, open protocol for establishing unique, private and secure connections between multiple parties without requiring the assistance of an intermediary “connection broker,” like Google, WhatsApp, an email provider, or a phone carrier. Secure connections are typically created by two or more peers creating and exchanging decentralized identifiers or “DIDs.” There are a variety of different implementations of DIDs, known as DID methods, available in the market, each with fundamentally different properties. Regardless of DID method, once two parties have exchanged DIDs, they can communicate securely as though through a private tunnel that nobody else can see or enter. This secure communication is facilitated by an umbrella of protocols known as DIDComm, which are based on a standard format known as JSON Web Message. DIDs can be created by anyone at any time, and you can have different DIDs for each of your digital relationships in order to keep them separate. DIDs provide secure connectivity; they do not by themselves provide trust — that’s where the second layer comes in.
- A standard, open “digital data watermarking” protocol for issuing, holding, and verifying protected data, including verifiable credentials or “VCs.” This enables anyone to verify the source, integrity, and validity of any data that is presented to them, and to do so robustly and securely. This mechanism uses well-proven public key cryptography to digitally sign each data element. Additionally, there are many interesting things we want to do with secure data, so this layer includes protocols for delegation of data, encryption, secure data storage, and approaches to revocation.
- Somewhere to store the public verification keys of connections and data owners. This allows anyone to locate and retrieve public keys at any time in order to verify the source, integrity, and validity of any data that adheres to the protocols in the previous layers. These keys and other cryptographic data are typically held in DID documents. While these could be stored in any database, in order for the source of information to be globally trusted, many decentralized identity systems have chosen distributed ledgers for their unique properties:
- no backdoor or admin access for malicious changing of data;
- no reliance on a single monopolistic provider that can turn it off, and;
- chronologically ordered so you know you are retrieving current keys.
Business & Legal
- A way to allow multi-party systems to establish transparent and standard rules around interactions. These rules are often developed as a trust framework, or a legally enforceable set of specifications & agreements designed for conducting transactions among a community of participants formed around a common purpose. Examples of systems that typically employ trust frameworks, also known as governance frameworks, include credit cards and electronic payments systems. Digital identity on the web will have to evolve to support digital trust frameworks of various sizes and purposes, as well as establish common patterns for mutual recognition of trust frameworks. In some cases, a trust framework may be defined in a very broad context, i.e. an entire sovereign nation. Other trust frameworks may be established for a particular community, context, or domain, such as healthcare or education.
For more information on this mental model, reference the 3 Pillars of SSI by Andy Tobin.
Organizations
There are a number of organizations working towards standardization of technologies that span across the web. Of these, there are a handful of umbrella organizations that are particularly important for those involved in building open standards for digital identity.
Decentralized Identity Foundation (DIF)
DIF is an engineering-driven organization acting as the center for development, discussion, and management of all activities required to create and maintain an interoperable & open ecosystem for the decentralized identity stack. DIF has the capability to set up IPR protected working groups, deliver specs and standards, and offer infrastructure for the community.
Notable Specifications: DIDComm 2.0, Well Known DID Configuration, Universal Resolver & Registrar, Identity Hubs, Sidetree Protocol, DID SIOP (Self-Issued OpenID)
World Wide Web Consortium (W3C)
At a high level, the W3C has been working on building web standards since the early 2000s. They’ve primarily focused on the development of the browser and have been instrumental in making browser interoperability possible. The organization was founded by Sir Tim Berners-Lee, who is widely regarded as one of the founding fathers of the internet.
Notable Specifications: CSS, HTML, XML, SVG, RDF, SOAP, DIDs, VCs, JSON-LD, ZCAP-LD, Linked Data Proofs, WebAuthn, CHAPI
Internet Engineering Task Force (IETF)
IETF is a standards development organization responsible for the general purpose standardization of core internet technologies. In particular, they focus on standards comprising the main Internet protocol suite, often known as TCP/IP. They promote a iterative, extensive, modular structure for standards development that allows internet technologies to achieve adoption and grow steadily.
Notable Specifications: URL, URI, URN, OAuth, JOSE (JWS/JWE/JWT)
Hyperledger
Hyperledger is an organization run by the Linux Foundation which promotes collaboration from a variety of industry stakeholders building implementations in open-source communities for a variety of use cases around decentralized ledgers and blockchains.
- Infrastructure for blockchain-agnostic, off-ledger, peer-to-peer interactions
- Consumes Ursa to provide decentralized key and secret management
- Shared cryptographic library enabling people (and projects) to avoid duplicating other cryptographic work and increase security
- Provides tools and libraries for building digital identity blockchains
- Sovrin is an instance of Indy
Notable Specifications: Anoncreds, DIDComm 1.0, DID Exchange, DKMS, Interop Test Suite, Chained Credentials, Rich Schemas, Data Overlays, Biometric Service Providers, ToIP-Stack
OASIS
OASIS is a non-profit consortium that brings people together to agree on intelligent ways to securely exchange information over the Internet and within their organizations.
Notable Specifications: SAML, XDI, KMIP, DKMS
Kantara Initiative
The Kantara Initiative is a nonprofit organization giving people agency over their personal data and the confidence to transact in the digital economy. Its goal is to offer service providers conformity assessment and assurance against well known standards and specifications while taking a user-centric approach to emerging industry and marketplace needs.
Notable Specifications: SAML, Identity Assurance Trust Framework, User Managed Access (UMA) 2.0, Consent Receipts
OpenID Foundation
OpenID Foundation is a special-purpose standards organization that was formed due to industry collaboration around digital identity technologies. OpenID Foundation has standardized several specifications around web-based digital identity technology.
Joint Development Foundation (JDF)
JDF is a nonprofit that provides turnkey infrastructure and efficient standards development processes to enable groups to quickly establish projects and gain momentum. It’s an umbrella organization that contains numerous different efforts. In addition to hosting DIF and many W3C members, the JDF is also integrated within the same infrastructure as the Hyperledger communities. After joining the Linux Foundation at the end of 2018, the JDF continues to push for new and interesting innovations with open standards and open-source implementations. The collaboration between the two organizations combines the standards development model of JDF with the resources, relationships, and scale of the Linux Foundation.
Trust Over IP Foundation (ToIP)
The ToIP Foundation is aiming to create the infrastructure necessary to support overlapping global ecosystems of verifiable digital trust on the web. They are defining a complete architecture for Internet-scale digital trust that combines both cryptographic trust at the machine layer and human trust at the business, legal, and social layers. They have a number of specific focus groups covering governance, technology, utilities, and ecosystems.
MyData Global
MyData is a global community focused on empowering individuals to exercise their rights when it comes to personal data. It’s an overarching effort with many independent sub-projects and focus groups in development such as MyData Operators. They share a common goal: to empower individuals with their personal data, thus helping them and their communities develop knowledge, make informed decisions, and interact more consciously and efficiently with each other as well as with organisations.
ID2020
ID2020 is a global alliance of organizations working towards responsibly implemented and widely accessible digital identity by the year 2020. This effort precedes much of the work on decentralized identity and SSI, however the group tends to embrace the idea of user-centric technologies and believes in their ability to transform the digital identity landscape. One of their key principles is that personal data should be portable, persistent, and private.
International Association for Trusted Blockchain Applications (INATBA)
INATBA offers developers and users of decentralized ledger technology a global forum to interact with regulators and policy makers and bring blockchain technology to the maturity and scale required for adoption. It’s a dynamic organization with many prominent members that serves as a platform to discuss and advocate for open standards, decentralized applications & services, and governance frameworks across the many different domains of the decentralized ecosystem.
Rebooting Web of Trust (RWOT)
RWOT is a twice annual design workshop focused on producing technical whitepapers to address issues impacting the future of decentralized identity systems and decentralized web of trust, including authentication & verification, certificate validation, and reputation assessment. It is a vendor-neutral setting open to participation from different tech groups and non-tech civil society members.
Internet Identity Workshop (IIW)
IIW is a bi-annual unconference taking place in Mountain View, California every year since 2005. It continues to be a valuable platform for finding, probing and solving identity issues in an open forum and has served as a breeding ground for collaboration around core identity technologies, including but not limited to OAuth, OpenID Connect, User-Managed Access, FIDO, DIDs, VCs, SSI, and decentralized identity systems.
Specs, Protocols, and Standards
Most specifications related to decentralized identity follow a similar path on the road towards standardization. Typically the stages are:
- Draft → serves as a proposal for a new standard, typically done by one entity
- Community Group → peer-reviewed by community members, adopted and developed by multiple parties in an open environment
- Working Group → dedicated and chartered group with a mandate to complete a specification
- Standard → completed specification, widely adopted and used by many industry partners
This process is more or less the same regardless of the organization hosting any particular standardization effort.
In addition, we can think of each specification as addressing one or more of the SSI “building blocks” that we described above. In some cases a standard may be a bridge between layers, enabling a closer link between connections, data, and keys, making the ecosystem more secure as a whole. What you will find below is a list of all relevant standards, links to every specification, the organizations they belong to, their relationship to the ecosystem, and their relative maturity as internet technologies.
https://gist.github.com/creatornader/c8a20c534d3cf8f65a9b34ce2ad81725#file-decentralized-identity-standards-md
This list will be maintained as a living document, capturing the current state of the decentralized identity ecosystem as it evolves.
Noteworthy SSI Projects
In addition to standards and specifications, there are a number of ongoing open-source projects built to demonstrate the impact of a truly decentralized, interoperable ecosystem, including test suites, reference implementations and more. Some of the most relevant projects are listed and described below in terms of their relationship to the SSI stack.
https://gist.github.com/creatornader/f0be7eaf53052b6d440bb0c08dd826ca#file-noteworthy-ssi-projects-md
This list will also serve as a living document, highlighting interesting new projects as the ecosystem matures.
If you have any feedback, e.g. comments, questions, or additions to this list, please reach out to the MATTR team at info@mattr.global or contact DIF at info@identity.foundation. We encourage involvement from the broader web community in any of the organizations covered in this article. If you are interested in learning more about these topics, you can subscribe to DIF’s monthly newsletter and stay tuned for more news.
Thanks to Balázs Némethi.